Key highlights:
- Three popular AMMs received 6.75 billion of risky funds in ETH, USDT, and USDC in a year.
- At least 270.34 million comes from hacks, darknet, address poisoning, and other illicit activities.
- Bad actors use CEXs to cash out laundered funds into fiat due to CEXs’ popularity, high trading volumes, and access to bank accounts.
In H1 2025, about 15% of hacked funds ($453 million) were directed to centralized exchanges, which remain the main off-ramp for illicit assets. DeFi platforms received a smaller share — $170 million (5.6%), or roughly ⅓ of the CEX volume.
In a year (between June 1, 2024 and May 31, 2025), three of the top 5 automated market makers (AMMs) by volume received 6.75 billion of risky funds in ETH, USDT, and USDC and sent 7.79 billion to risky sources. These risky sources include high-risk exchanges, gambling, mixing services, cross-chain protocols. Out of these funds, illicit funds from hacks, darknet, address poisoning, and other illegal activities account for 270.34 million in incoming transactions and 690.08 million in outgoing transactions.
Even with much lower illicit volumes compared to CEXs, AMMs expose clear patterns of misuse. Here are the top three.
Popular tactics illicit actors use to launder crypto
1. Malicious smart contracts for executing exploits
A frequent attack vector in DeFi comes not directly from AMMs, but from vulnerable protocols built on top of them. In H1’25, contract exploits accounted for 69.75% of hacks. Here is just one of the notable examples:
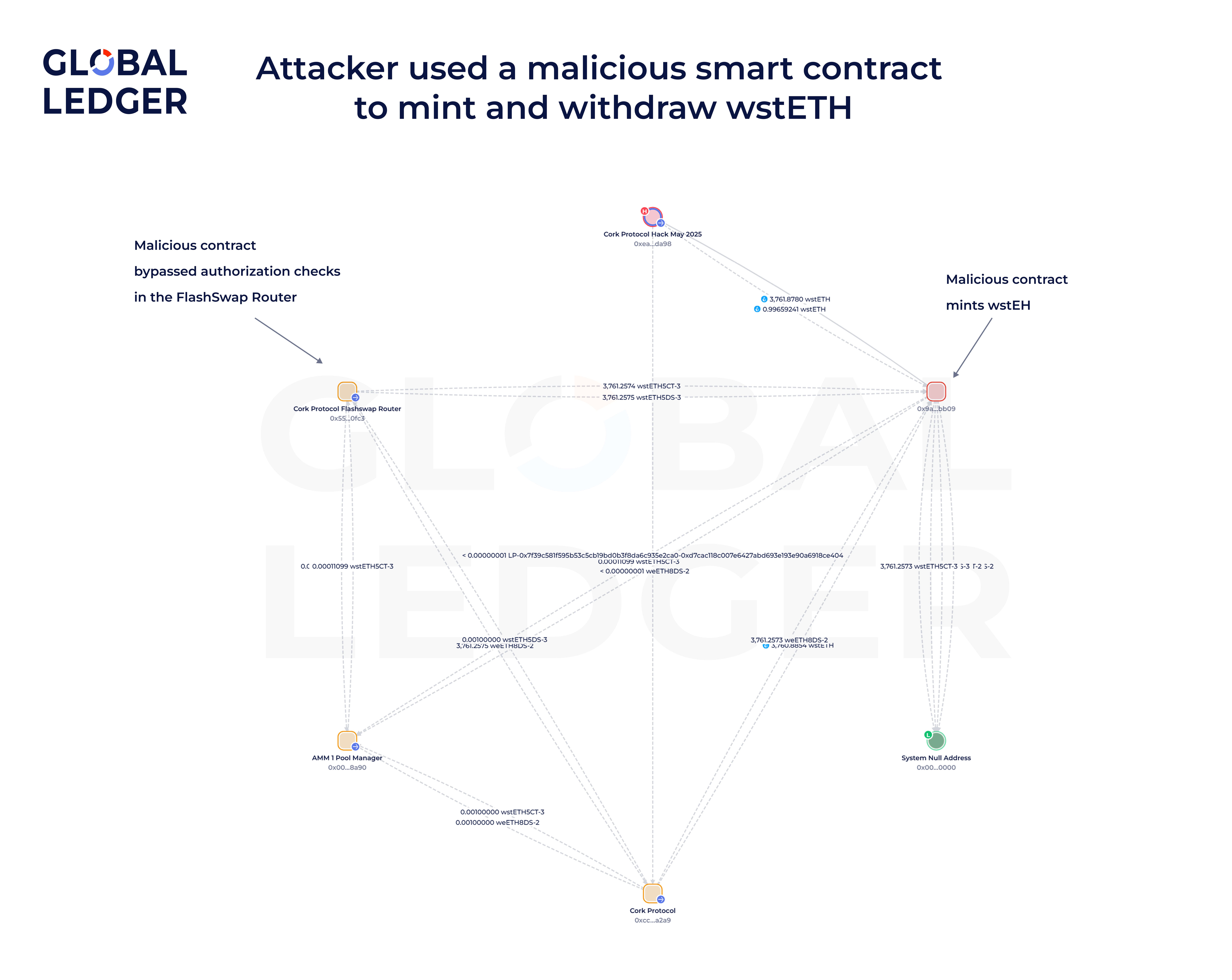
On May 28, 2025, when the Cork Protocol’s wstETH:weETH liquidity vault was targeted. An attacker executed a sophisticated dual-vector attack that culminated in the unauthorized extraction of approximately 3,761 wstETH (~$12 million) in under 17 minutes.
How the exploit unfolded:
- The attacker deployed a malicious hook contract to manipulate Cork’s logic, bypassing authorization checks in the FlashSwap Router, which was built on AMM’s periphery code.
- This exploit allowed instantaneous minting and withdrawal of wstETH — a wrapped staking token — without proper verification.
- Within minutes, the stolen wstETH was swapped for ETH using AMM.
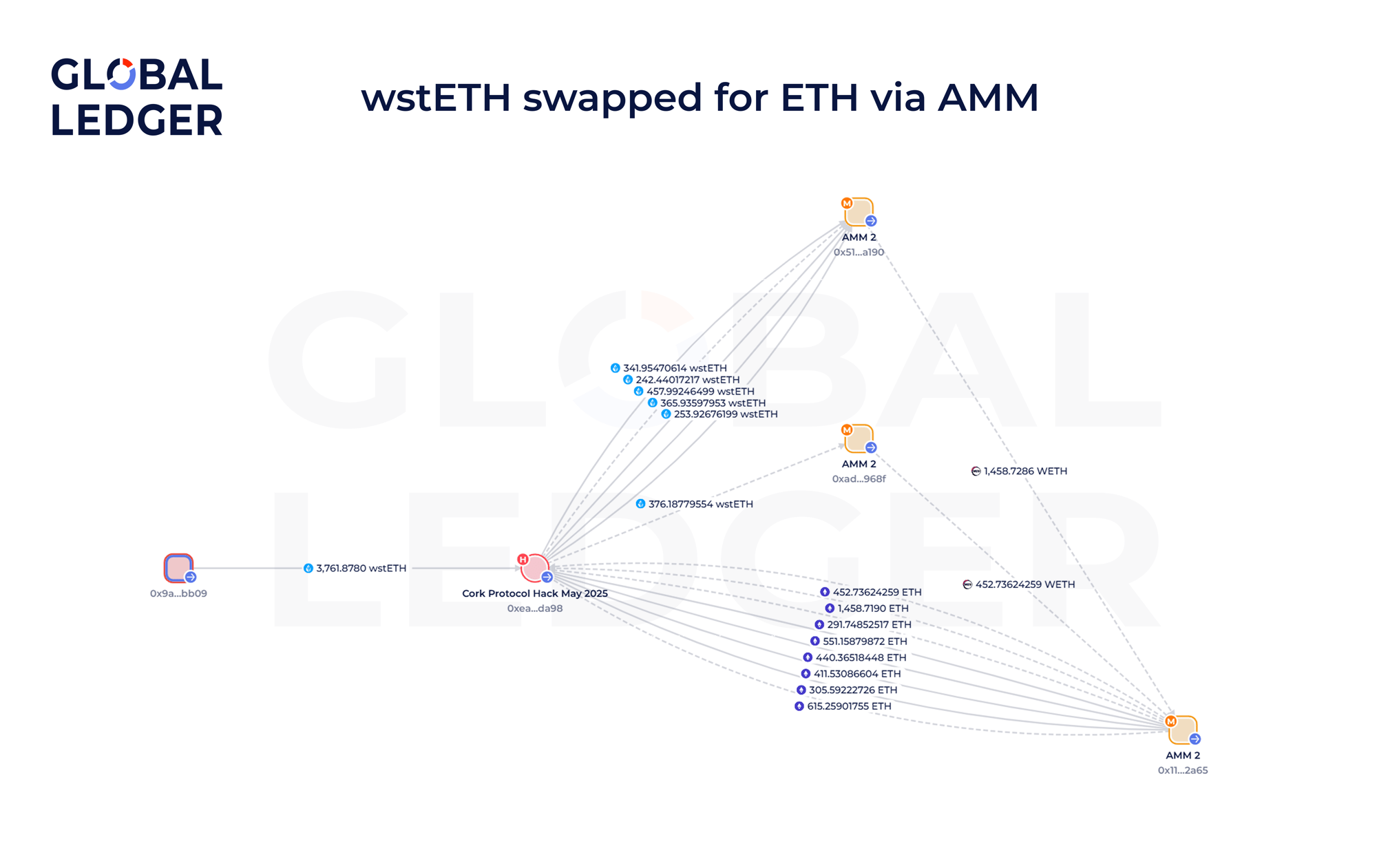
Even though the AMM itself was not the point of failure, the attacker exploited infrastructure built on top of it — manipulating Cork’s smart contracts to extract funds. They then used an AMM to convert the stolen tokens into fungible ETH. This case illustrates how a single exploit can involve multiple AMM interactions.
2. Swapping low-liquidity tokens into ETH
Another common laundering tactic involves converting low-liquidity tokens — often minted illicitly or stolen — into more liquid assets like ETH. The Meta Pool exploit from June 17, 2025, illustrates this pattern clearly: attackers exploited a flaw in Meta Pool’s “fast unstake” feature, minting approximately 9,700 mpETH (a staking derivative, in theory, worth $27 million).
However, due to extremely limited liquidity in mpETH markets, only about 15.29 ETH (roughly $39,450) could be swapped before prices collapsed, and the pool was drained.
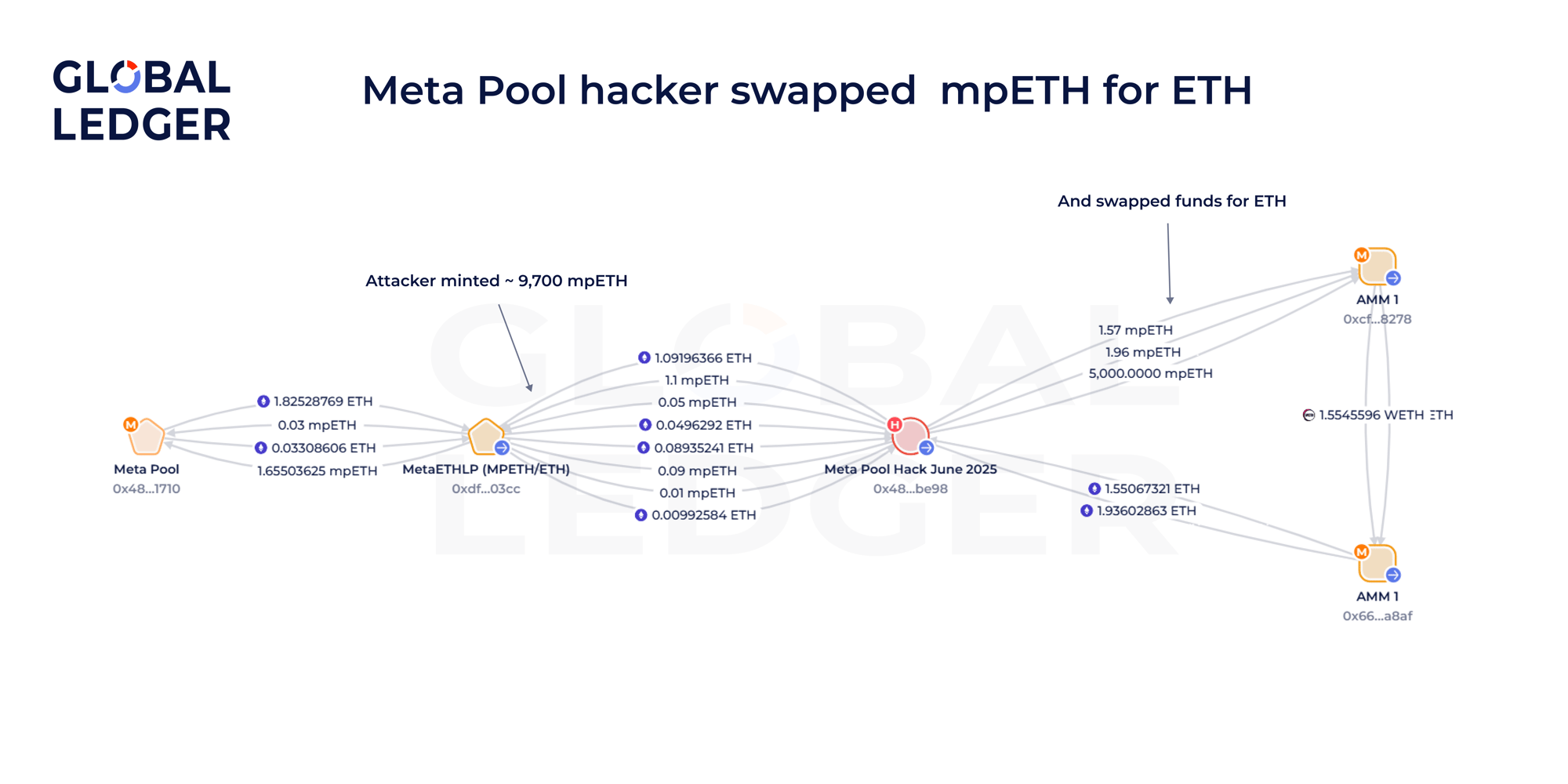
This case highlights two critical issues:
- Price impact and slippage: Low liquidity means any large swap dumps the token price and limits what attackers can actually cash out.
- Rapid swapping to liquid tokens: Even though full value cannot be extracted, attackers still convert stolen tokens into ETH or other liquid assets — often using AMM pools — before moving funds further along laundering chains.
Despite minting a high token volume, the laundered value was limited by market depth. This pattern demonstrates how illicit actors exploit AMMs for quick asset conversion — even when facing liquidity constraints — before routing proceeds through mixers, bridges, or exchanges.
3. Using liquidity pools to obscure and grow illicit funds
Another common tactic employed by illicit actors involves depositing stolen assets into decentralized liquidity pools, temporarily locking funds in exchange for LP tokens. These positions can generate passive rewards and are often held for days, weeks, or even months before being redeemed.
A notable example is the wallet, connected to the Multichain exploit. While its visible token balance is around $73,800, its total net worth exceeds $5.6 million, primarily due to various liquidity positions held across AMMs like Aave, Spark Fi, Stake DAO, Ether.fi, Symbiotic, Uniswap, and Curve.
In one example of a transaction, the address deposited 399,945.5286 USDT into a pool (comprising DAI/USDC/USDT) and received LP tokens representing ownership of a portion of the pool.
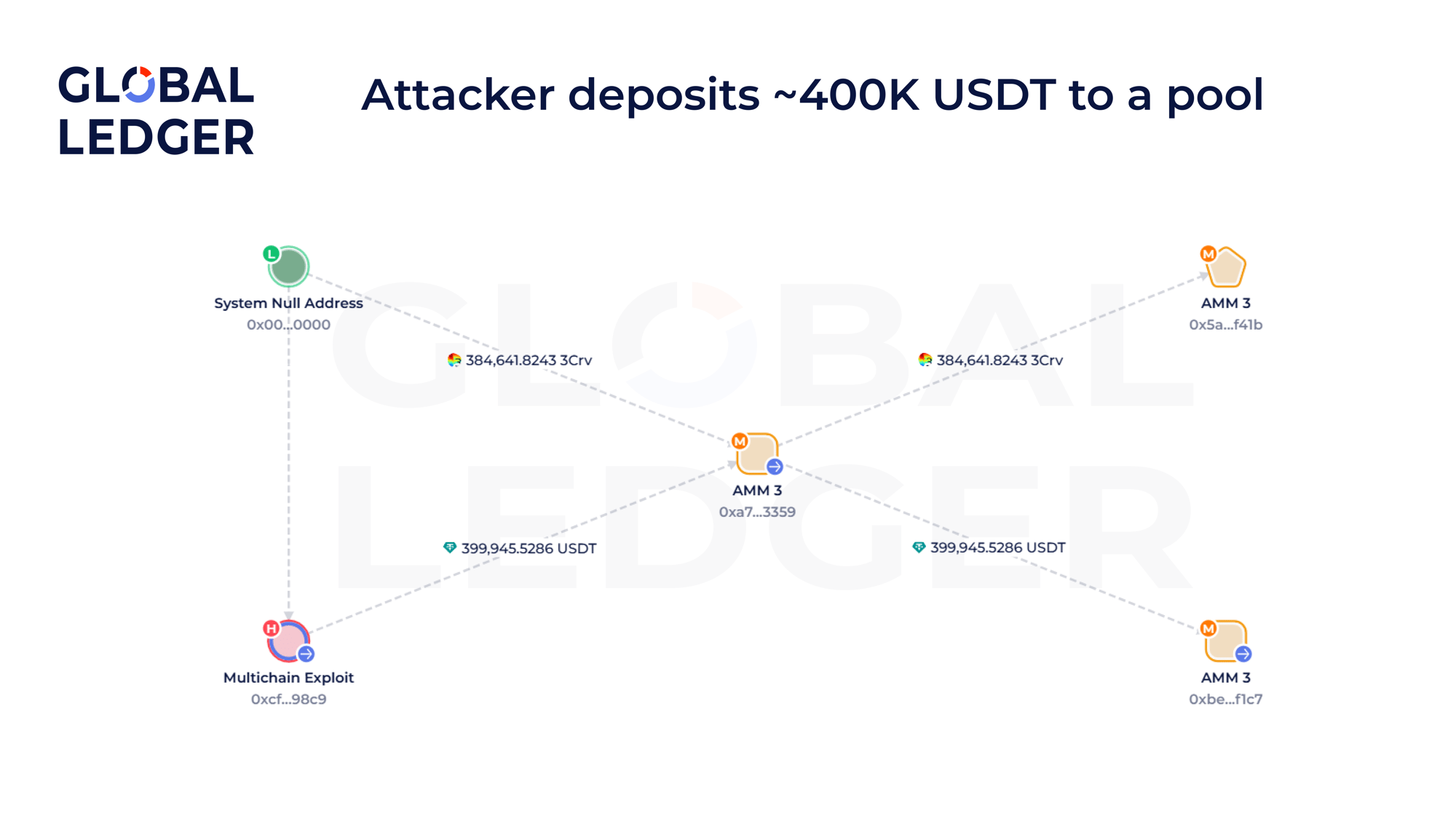
These LP tokens can later be redeemed for the underlying assets, which may differ from the original deposit, enabling a form of internal DeFi mixing.
Eventually, the wallet unpooled the funds and received:
- 39,404.4289 MIM (~$39,430.72)
- 27,148.1648 DAI
- 26,797.5807 USDC
- 8,384.7497 USDT.
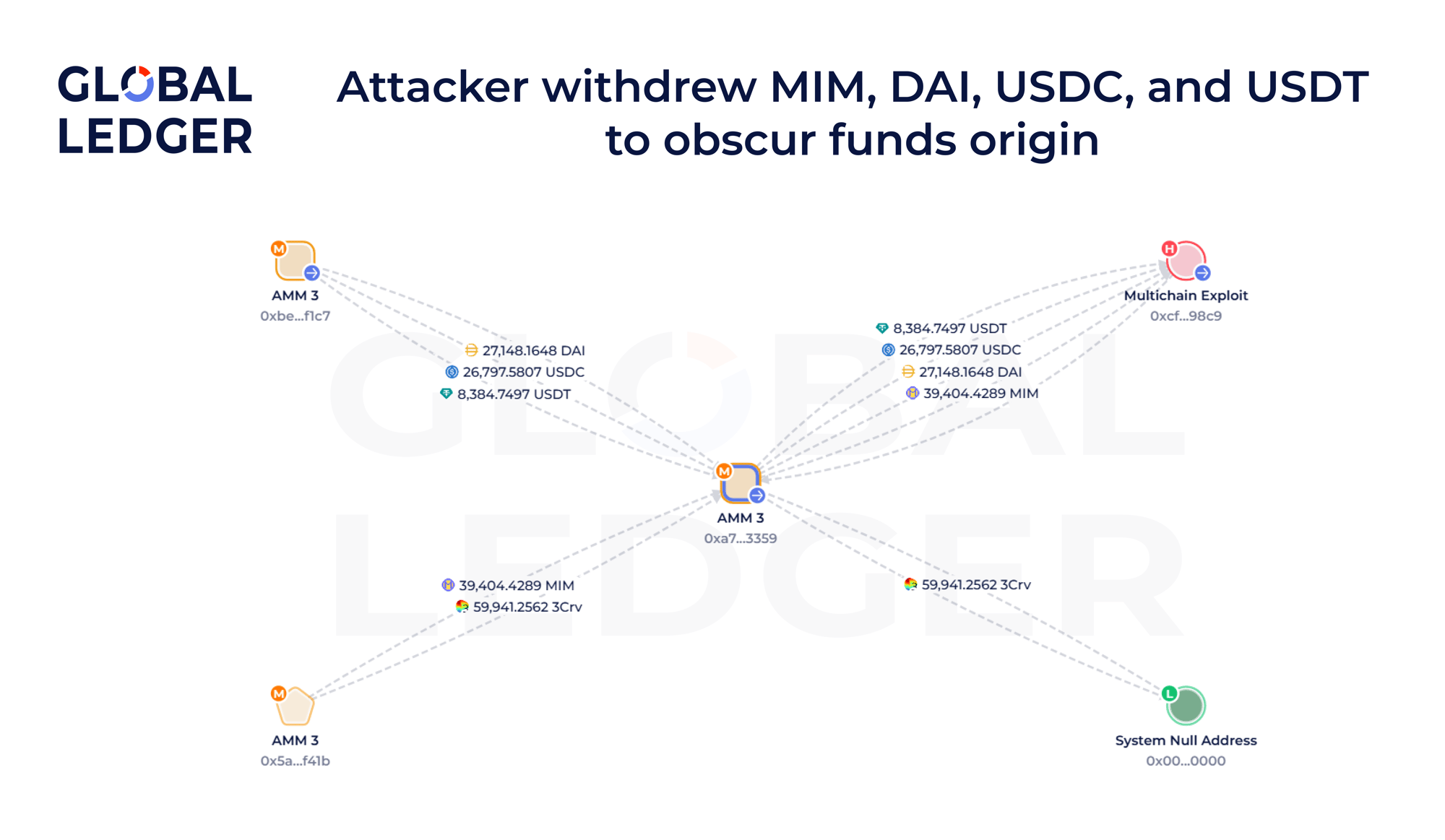
This conversion of one asset into several others breaks the traceable link between the input and output, obscuring fund origins.
Additionally, the same wallet claimed 9,326.5874 CRV (~$7,351.03) in staking rewards, showing how actors not only launder assets but may also collect protocol rewards during the process.
VASPs unintentionally become a major target
These are just three popular examples of how DeFi gets pulled into money laundering. This happens because DeFi’s open and permissionless nature makes it vulnerable to misuse. AMMs are where bad actors turn stolen or illiquid assets into popular assets to hide the trail and finally cash out via CEXs.
If VASPs can’t see how funds’ origin was obscured, they risk accepting assets that look clean but are actually linked to hacks, scams, sanctioned entities, etc. For example, in 2024, 177 licensed entities processed ~57% of Garantex funds. Our research showed that $6.51 billion was sent to/from 88 VASPs with EU licenses. They account for 78.8% of all licensed entities’ exposure.
One more prominent example is HuiOne. Approximately 942.9 million USDT was transferred from HuiOne wallets to major centralized exchanges on both the Tron and Ethereum networks.
Notably, low-risk exchanges appear significantly more exposed to illicit flows than high-risk ones. This might be due to CEXs’ popularity, high trading volumes, and access to bank accounts, enabling them to cash out funds into fiat. Additionally, regulated platforms can unintentionally act as normalization layers. Criminals use medium- and low-risk exchanges to blend illicit funds with legitimate activity, taking advantage of their reputation for safety to reduce oversight.
What can be done?
Key steps to improve AML/CTF efforts include:
-
Strengthen risk assessment protocols
-
Apply stricter measures to review transactions
-
Use advanced tools to track the movement of funds.
Global Ledger supports each of these areas with speed-first solutions — from transaction tracing, real-time risk scoring, and automated alerts to comprehensive entity exposure reports and complete entity profiles.
 KYT Tool
KYT Tool
 KYB Tool
KYB Tool
Worried about missing critical risks? Global Ledger helps you see everything in context.
 The Nobitex Hack: More Than Meets the Eye
The Nobitex Hack: More Than Meets the Eye
 Ukraine Could Collect $202 Million in Taxes from Crypto Industry
Ukraine Could Collect $202 Million in Taxes from Crypto Industry