Key Highlights:
-
The Nobitex hack on June 18, 2025, reported a $90M loss across eight blockchains.
-
However, blockchain analysis shows that many of Nobitex funds were quickly moved rather than lost, including approximately $187 million transferred shortly after the breach.
-
Long-term laundering-like behaviors were uncovered, pointing to months of fund obfuscation tactics.
-
Patterns include the use of peelchains and one-time intermediary wallets.
Sometimes, a single event brings long-standing issues to the surface. When the Nobitex hack made headlines, it initially seemed like a familiar story — a major breach, lost funds, and shaken trust.
As the Global Ledger team traced the on-chain activity during the Nobitex investigation, a more complex story began to emerge. Beneath the surface, our research team found signs that unusual fund movements had been happening for months, well before the attack — and continued even after it.
Even now, after the breach, Nobitex appears to retain control over a significant portion of its reserves — a detail that changes the nature of the story. Before diving into what we discovered, let’s step back and revisit how this all began.
About the hack
On June 18, 2025, Nobitex — one of Iran’s largest cryptocurrency exchanges — experienced a severe cyberattack that spread across multiple blockchains. In total, around $90 million in digital assets were destroyed, with funds sent to so-called burn addresses, making them irretrievable.
Shortly after the incident, a pro-Israeli group called Gonjeshke Darande (also known as Predatory Sparrow) publicly claimed responsibility.
However, while much of the focus was placed on the attackers, our research pointed to deeper issues that predated the breach.
Obfuscation behind the curtain: not a hack alone
How laundering-like activity came to light
As our team followed the on-chain trail from the Nobitex breach, we uncovered more than just stolen funds. While tracing one address tied to Gonjeshke Darande — 1FuckiRGCTerroristsNoBiTEXXXaAovLX — we noticed repeated interactions with wallets belonging to Nobitex itself and patterns that looked a lot like laundering.
We began to see signs of long-running peelchain activity: large amounts broken into chunks, routed through chains of “short-lived” wallets, and eventually landing on exchanges or service providers.
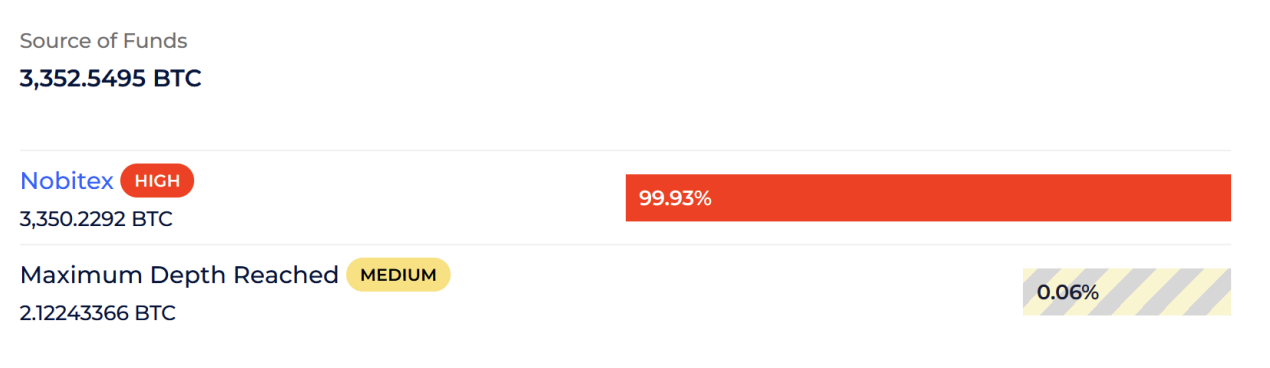
Following the money backward, we found one address — bc1q…rrzq — where the suspicious fund movement started. To figure out who owned it, we checked all the wallets that sent money to it via the counterparty report. Almost all of them were connected to Nobitex.
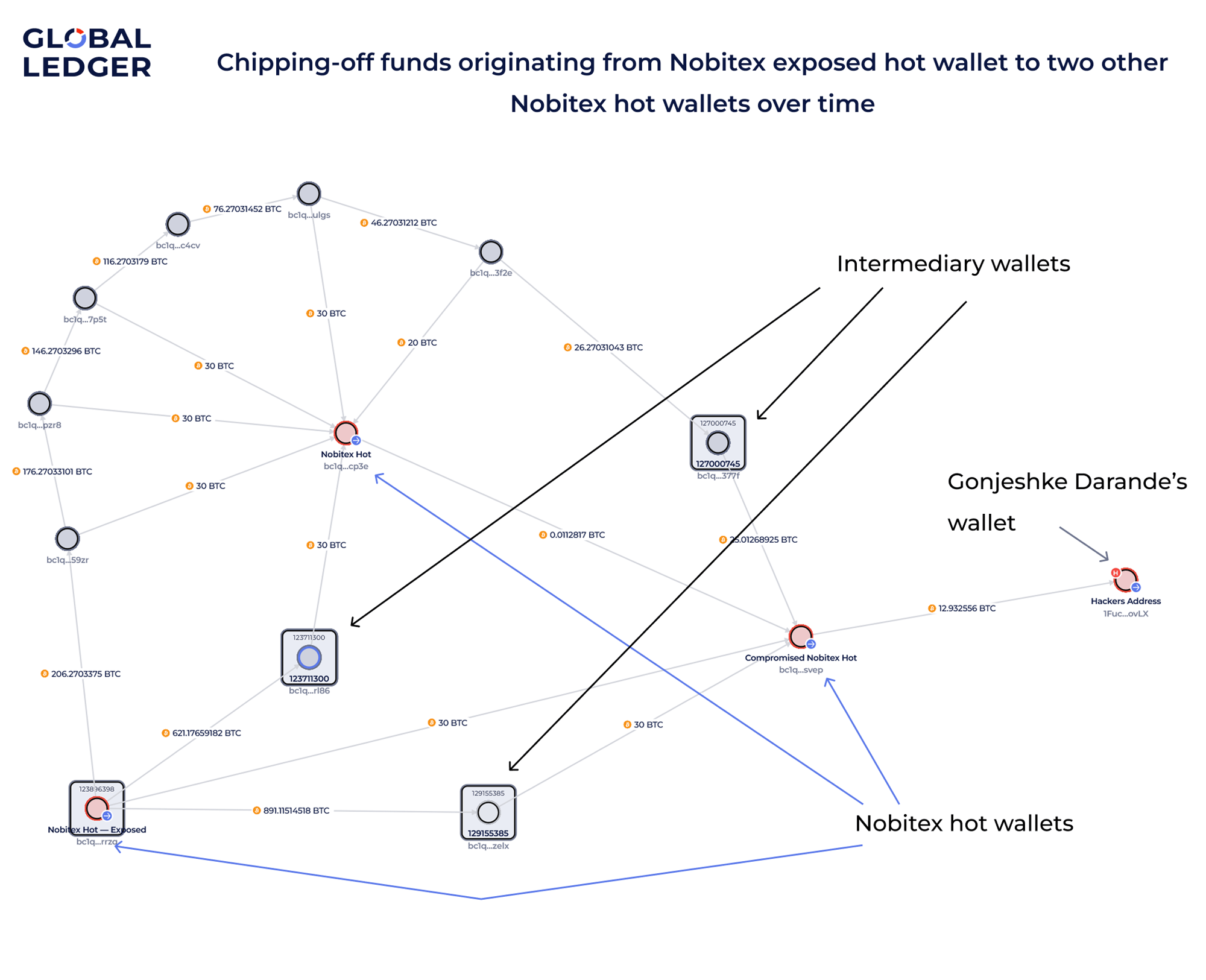
Hidden flows and lifespan wallets
The laundering scheme included more than just peelchains. We also observed another common method used by centralized exchanges: moving funds between internal wallets that are only active for a short time. In this case, when one Nobitex hot wallet completed its cycle, it passed its remaining balance to another — including the wallet later compromised in the hack.
This short-lived, “pass-the-baton” behavior was consistent across multiple chains, including Tron.
By this point, the picture was becoming clear. Three key hot wallets, including the one drained in the hack, had been consistently passing BTC through intermediary addresses, usually in 30 BTC chunks — long before June 18. The intent seemed to be reducing traceability, not emergency action.
What’s more, shortly after the hack, Nobitex announced it had moved remaining funds from unaffected hot wallets as a precaution.
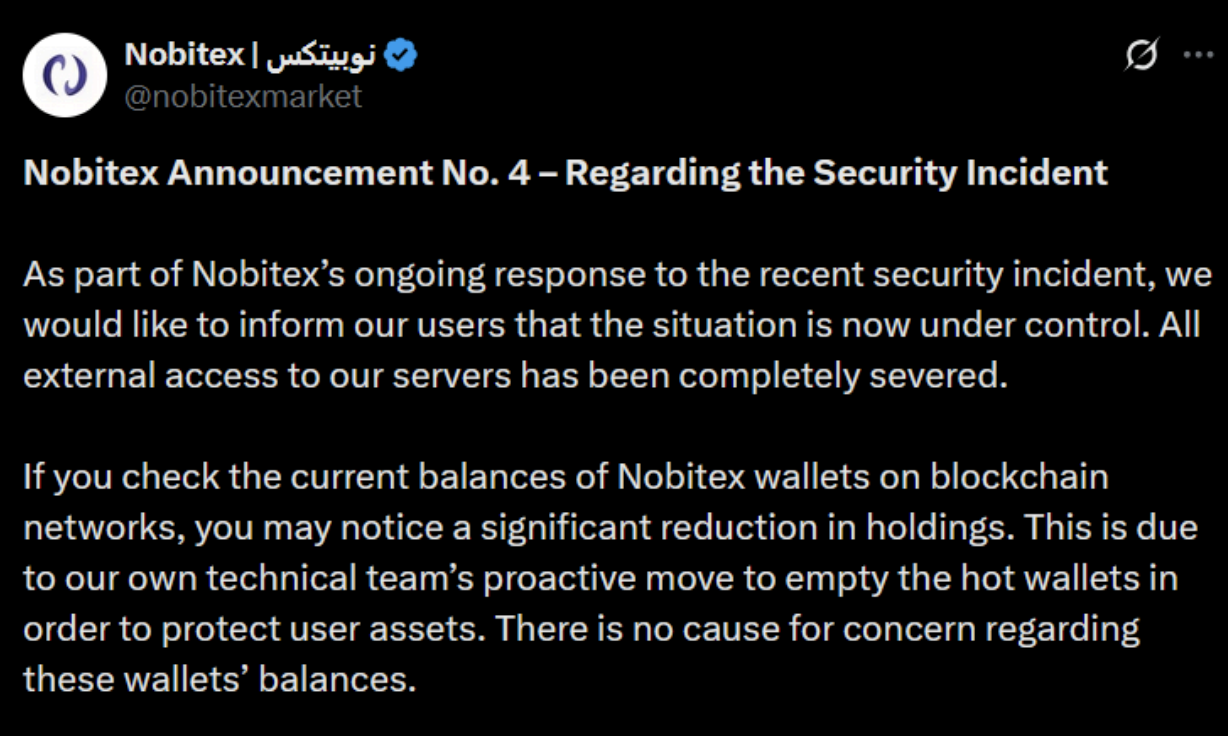
That’s exactly what we observed next on-chain, as one of Nobitex’s exposed hot wallets moved its remaining funds. But was it really a security measure or still part of the plan?
Post-hack fund movements
About eight hours after the attack on June 18, Nobitex’s exposed hot wallet and a few other internal wallets performed a major transaction:
- 1,801 BTC ($187.5 million) were moved into a new address bc1q…qq53.
- From this address, they were sent again to what is believed to be a rescue wallet (you can find more information on this below).
- On June 19, another 1,780 BTC were moved into a “fresh” wallet bc1q…7hpy, followed by a smaller 3 BTC transfer.
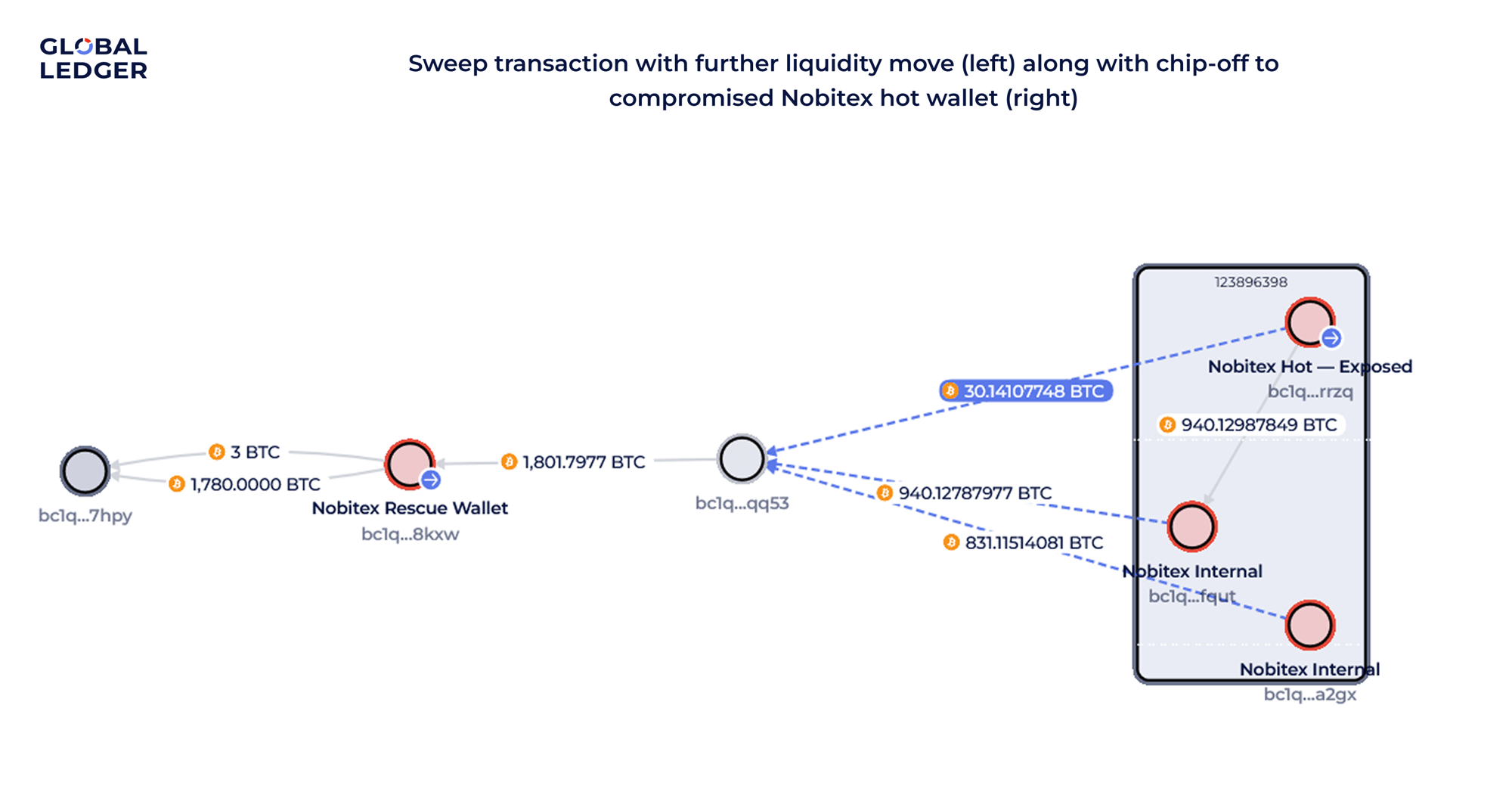
What’s the rescue wallet?
This wallet has been acting as a consolidation one. Our analysis showed that the rescue wallet:
- Has been active since October 2024
- Regularly received chipped-off amounts, often in 30 or 20 BTC chunks
- Continued the same chain-like distribution pattern seen across Nobitex’s infrastructure.
What does this all mean?
Rather than a single, contained breach, the data points to a deeper, ongoing practice:
- Long-term use of peelchains
- Lifecycle “handovers” between hot wallets
- Patterns that reduce traceability across multiple chains
- Fund flows that blur the line between day-to-day operations and obfuscation.
The final piece came when Gonjeshke Darande published documents on June 19, challenging Nobitex’s explanation of how funds were recovered.
And by June 20, we saw another large liquidity transfer to a wallet linked to Nobitex’s earlier infrastructure — right after they’d promised “protective measures” for user funds.
The Nobitex hack: lessons learned
Sometimes, it takes a crisis to reveal what’s been quietly at risk all along. The Nobitex incident didn’t just highlight technical vulnerabilities; it also revealed operational patterns that had gone unnoticed for months.
For regulators, compliance teams, and VASPs, the takeaways are clear:
- When fund flows are hidden, risk grows quietly. Laundering-like behaviors, like peelchains or quick wallet handovers, can become part of day-to-day operations — until a breach reveals how deep they run.
- Monitoring early means reacting less later. Some warning signs were visible well before the attack. Continuous on-chain monitoring could have raised red flags sooner, possibly softening the impact.
- Transparency protects more than your reputation. Being able to demonstrate where funds go — and why — builds trust with regulators, partners, and users.
- Clarity is critical — especially in a crisis. Many users were left confused after the hack. That’s why open and timely communication is essential for preserving user trust, especially in regions where crypto fills real financial gaps.
What’s next
Thanks to on-chain forensics, we now understand how certain behaviors — like fund chipping, laundering-like flows, or fast-moving wallet cycles — can quietly signal deeper risks. Some of these patterns don’t always mean misconduct, but they do deserve attention.
At Global Ledger, we're not here to “point fingers” — we're here to help you spot issues early, so you can stay ahead instead of reacting after the fact.
If you're operating in the crypto space today, here are a few things worth keeping in mind — especially when it comes to staying ahead of risk and building trust:
-
You don’t have to wait for a breach to understand your exposure.
-
You’re not alone in managing compliance, transparency, or reporting.
-
You can face scrutiny with confidence when you have visibility.
With the right tools, you can stay ahead instead of only reacting after the fact. Global Ledger can help your team spot risks early through blockchain visualization technology, smart AML risk scoring, and complete counterparty insights. We’re here to support you with clarity and confidence as you manage risk in a fast-moving environment.
 Crypto Clues in the Teen Spy Case: Beyond the Reuters Story
Crypto Clues in the Teen Spy Case: Beyond the Reuters Story